In the evolving landscape of the legal industry, the management of electronically stored information (ESI) has become a focal point of discussion and strategy. With the digitization of records and communications, legal professionals are increasingly faced with the dual challenge of handling both private and public forms of ESI, such as emails, cell phone records, websites, and social media accounts as evidence in court. The growing attention to online evidence emphasizes the need for a nuanced understanding of its collection and preservation, particularly in the face of legal proceedings. In this webinar, Alex Sappington, CEO of Page Vault walks through tips for handling public ESI as evidence.
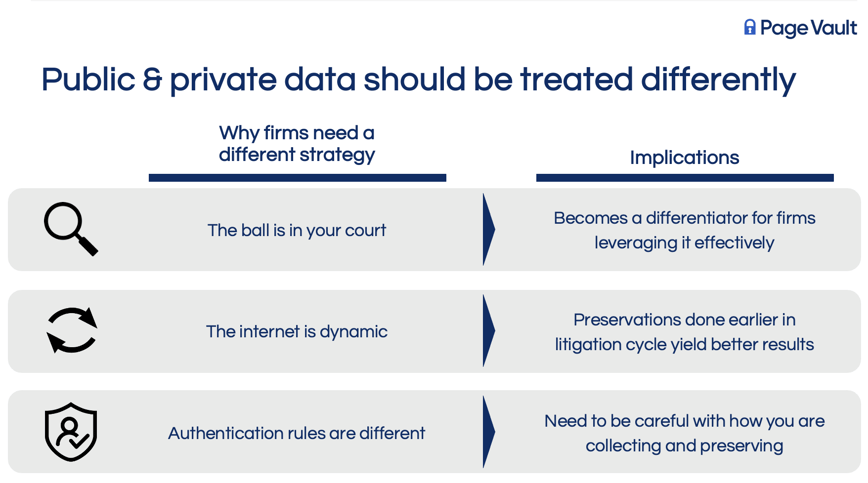
The distinction between private and public ESI highlights different challenges and strategies required for their management. Private data often comes into play in eDiscovery, requiring parties to exchange relevant information as part of the litigation process. Private data includes information found in email, messaging and collaboration applications, mobile device data, and more. In contrast, public data encompasses information freely available online but requires proactive measures for its collection and preservation due to its dynamic and ephemeral nature. Public data is found on websites, social media platforms (i.e. Facebook, TikTok, Twitter, Instagram), and video sharing platforms (i.e. YouTube). The legal industry's approach to managing public ESI calls for a strategic and timely collection to ensure valuable evidence is not lost.
As opposed to private data, the transient nature of public internet content adds urgency to collection efforts, as potentially crucial evidence can quickly change, be removed, or be made private, at which point legal teams in civil matters have little recourse to recover the information. As such, evidence preservation for public data done earlier in the litigation process yields better results. However, the authentication rules differ for public and private data. Legal professionals must employ meticulous methods to collect and preserve public online evidence, ensuring its authenticity can withstand heightened judicial scrutiny compared to private data.
Online evidence holds significant value across various legal practice areas, demonstrating its versatility and critical role in modern legal challenges. From intellectual property disputes and labor litigation to family law and criminal investigations, the strategic use of online evidence can be decisive in proving a case. Examples of its application include substantiating trademark and copyright infringement, verifying claims in employment disputes, and supporting cases in pro bono work, highlighting the diverse impact of online evidence in legal outcomes.
Relevant case examples include:
Intellectual Property: Disney v. Sarelli, Specht v. Google
Criminal: Commonwealth v. Mangel, People v. Lenihan
Employment: Meth v. Natus Med. Inc, Vasquez-Santos v. Mathew
The collection and use of public online evidence are governed by legal rules, notably the Federal Rules of Evidence 901 and 902, which outline the requirements for the authentication of electronically stored information. Recent amendments have facilitated the process, allowing certain types of ESI to be considered self-authenticating. This shift reduces the need for witness testimony but places greater importance on providing detailed affidavits and metadata documentation to establish the credibility of online evidence. A sufficient affidavit includes: 1) Detailed information about the collection process and 2) Certification of a Qualified Person. The “qualified person” is the person who is in the digital chain of custody. This is often the collecting employee, collecting third party, or the self-authenticating software in which the evidence was collected.
As the amount of evidence publicly available online continues to rise, many attorneys use simple screenshot tools or print-to-PDF to collect this type of evidence. While these tools are low-cost or even free, they don’t keep users out of the chain of custody and are difficult to authenticate as they often lack supporting metadata or may produce low-quality images. This approach is typically on an ad-hoc basis where law firms do not have an established collection policy in place, creating firm-wide risk.
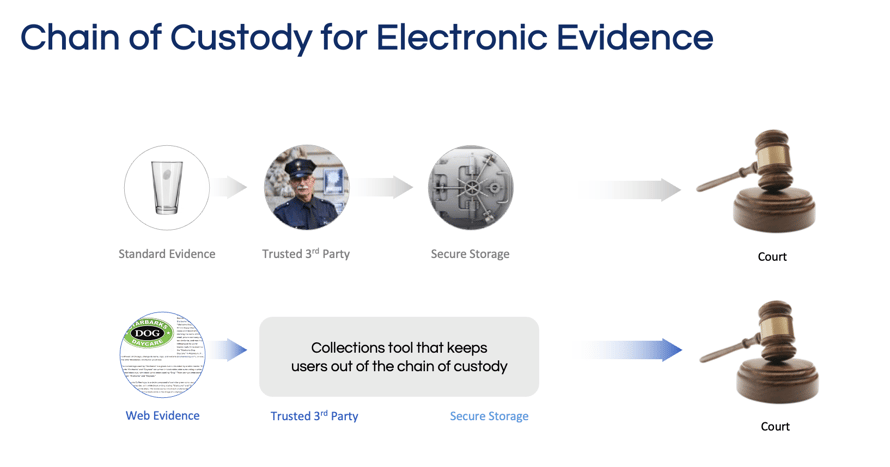
Given the complexities of collecting online evidence, legal professionals should avoid being in the chain of custody altogether. To do so, attorneys and paralegals should take a structured approach involving a third-party vendor or a self-authenticating technology like Page Vault, which keeps users out of the chain of custody. Noteworthy drawbacks of relying solely on an outsourced digital forensic vendor for evidence collection are delayed turnaround times and often costly services. Using a self-authenticating tool addresses the need for both efficiency and reliability in the collection of online evidence, enabling a proactive and cost-effective approach to legal challenges. Page Vault offers both outsourced solutions and self-authenticating software. Firms should weigh the complexity of the evidence collection against internal resources to determine if outsourcing or software is the best choice for them for a particular project. Many firms leverage a combination of both outsourcing and software.